Risk Assessment & Multi-Criteria Decision Techniques Essay.
The multi – Criteria Decision Techniques as well as risk assessment are discussed under this section. The comparison of multi-criteria decision making to that of risk assessment are thoroughly done.
Risk Assessment Methods
The technological scientific process base that is consisting steps of risk analysis, identification of the risk as well as risk evaluation is refers to as Risk assessment.
Accordingly, CVSS stand as the best option for risk assessment due to the fact of its capability which is focused in calculating various different types of scores such as temporal, base and environment. Risk Assessment & Multi-Criteria Decision Techniques Essay.
ORDER A CUSTOM-WRITTEN, PLAGIARISM-FREE PAPER HERE
This is applicable to be adopted as a risk assessment for a technology based applications such as NFC. Meanwhile, OCTAVE only focuses on organizational risk as it is designed for organizations instead of technological risk and, it is hard to implement because there are many practices that need to implement. Although, CVSS does not reduce the number of attack, it evaluates the attacks with rating score [13].
Multi Criteria Decision Making (MCDM) Methods
This is a decision making algorithm which is utilized in making best decisions in the alternative decisions. Its main aim is to determine and rate the alternative decisions in terms of there priorities. This technique has been used for many assessments. From the study, MACBETH and the AHP are used in supporting the pairwise comparisons. Risk Assessment & Multi-Criteria Decision Techniques Essay. TOPSIS is utilized when the ideal as well as the anti ideal options are needed. ELECTRE and VIKOR, all the two are based on the same principles on the concordance analysis like considering some global measures as well as other criteria which are [13]. SMAA makes determination if the information of the decision is correct and accurate which in-turn helps in preventing making of wrong decisions because of inadequate information. The MCDM method gives a description that those AHP applications, have powerful and highly flexible guidance method to the techniques used for decision making. Risk Assessment & Multi-Criteria Decision Techniques Essay.
Possibility and Impact Estimation of Vulnerabilities using CVSS
Calculation of possibility is done by the use of metrics group as well as temporal group metrics of the CVSS. Calculation of Impact estimation is done by use of base group metrics as well as environment group metrics of the CVSS [9]. There results are taken from the survey data which needs respondents for evaluation. The survey data is categorized into discrete probability distribution which is used in assigning the probabilities for every outcome of each and every rating group as low, medium as well as high for the CVSS. The scores in this case segregated into a probability distribution because the participants had different values for each and every CVSS metric. The calculation of probability is given by the formula below;
SMAA-TRI method is used in calculation and production of category indices which are acceptable for each and every pairs of the categories and alternatives. The JSMAA is used for simulation of the SMAA-TRI [9].
FINDINGS
Dos Attack & Data Corruption Attack Countermeasures & Selection Using Mcdm
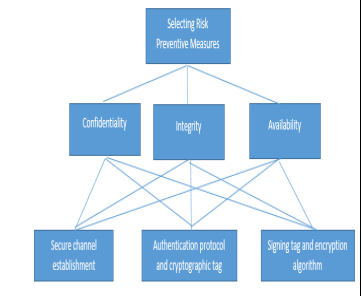
The Dos attacks takes place when the NFC devices gets in touch of the empty or rather NFC tags which are corrupted, error messages will take the NFC devices until such a time when the devices are suspended. This also takes place in smartphone which NFC enabled. Corruption od data involves the processes whereby the attackers manipulate data as a results the NFC transmission is disturbed by the NFC interfaces and the devices. Now that data has been corrupted, it will be unreadable to the devices which are operating under the NFC [10]. In order to prevent corruption of data, then NFC devices have to observe and check the radio frequencies when data is being transmitted. Detection of this particular data corruption attacks can be done due to the fact that higher power is required in the corruption of data as compared to sending of data, therefore, NFC is in a position of detecting sending data session which utilizes more power during transmission of data. This measures which are to be used in minimizing the risks of corruption of data as well as the Dos attacks is done by signing tags which encryption techniques by the use of cryptographic tag authentication protocols as well as establishment of a secure channel which has to exist between the NFC devices. It is the best option to secure the NFC communication as well as defending all types of data attacks when communication or data transfer is taking place [10].
MCDM Analysis is AHP Approach
This AHP method of approach utilizes the selection of the NFC risk countermeasures which have the highest priority. This method is utilized in creation of the priorities the alternatives and its criteria is utilized in decision making as well as judgmental for the alternative decisions made. The AHP method comprise of the following steps [11];
ORDER A CUSTOM-WRITTEN, PLAGIARISM-FREE PAPER HERE
- Step 1
Development of criteria weights for the creation of single pairwise comparison matrix for that [articular criteria.
- Step 2
Development of the ratings for every decision alternative made for every criterion by development of the pairwise comparison matrix
- Step 3
Calculation of the average weighted rating for each and every decision alternative. The decision alternative which has the highest score is chosen.
In the AHP method, the pairwise comparisons are utilized in establishment of the relative priority for every criterion which is against another criteria or that is against the decision alternatives. The table below shows the AHP scale which utilizes the ratings from the equal importance to the extreme importance.
| Scale of Importance | Explanation |
| 1 | All with same importance |
| 3 | One is slightly important compared to another |
| 5 | One is just important to another |
| 7 | One is very important compared to another |
| 9 | One is completely important compared to another |
| 8,6,4,2 | When compromise is required |
From the table above, a hierarchy of decision is designed for the purpose of making decision on the highest priority countermeasures of the NFC. On comparison in order to know give the confidentiality, establishment of the secure channels is considered as very crucial as compared to use of the authentication protocol or the cryptography. On the other hand, the use of the protocol is considered to be more important as compared to use of encryption. From the comparison above, the establishment of the secure channel as a priority of 0.7611, utilization of the protocol has a priority of 0.1663 and the use of the tags containing the encryption has a priority of around 0.0726 [11]. Risk Assessment & Multi-Criteria Decision Techniques Essay.
On the comparison for provision of integrity, it is seen that establishment of secure channel is regarded as more important as compared to the cryptography as well as the authentication protocol. As compared to the protocol, the establishment of the secure channels is also considered more important. However, utilization of the protocols is slightly important as compared to signing of the tag using the encryption. The establishment of a secure channel is prioritized at 0.7503, the utilization of the protocols is prioritized at 0.1714, as finally the use of the signing tags in encryption is prioritized at 0.0782 [11].
When comparing priorities in terms of availability provision, it is noted that the establishment of a secure channel is regarded as more important as compared to the use of authentication protocol as well s the cryptography. The establishment of a secure channel is also regarded as more important as compared to the use of protocol. However, the use of protocol is noted to be slightly important as compared to the use of signing tag with the use of encryption. The establishment of secure channel is prioritized at 0.7172, the utilization of the protocol is prioritized at 0.1947 and the utilization of signing tag by the use of encryption is prioritized at 0.0881 [11]. Risk Assessment & Multi-Criteria Decision Techniques Essay.
TABLE 6 HERE
| Alternatives | Integrity | Confidentiality | Availability | Priority |
| Priority 1 | 0.7503 | 0.7611 | 0.7172 | 0.7429 |
| Priority 2 | 0.1663 | 0.1714 | 0.1947 | 0.1775 |
| Priority 3 | 0.0726 | 0.0782 | 0.0881 | 0.0796 |
The overall priority of the AHP for every alternative as shown in the able above is calculated using all the pairwise comparison of alternatives in accordance to CIA.
The highest priority which is obtained by the calculations of the AHP is aimed to establish a secure channel which is having a priority of 0.7429 that when converted to percentage, it comes to 74.29%. Measures of prevention like the use of cryptography as well as the authentication protocol is also prioritized at 0.1775 which is equivalent to 17.75 %. The signing tag using the encryption algorithm is prioritized at 0.0796 which is equivalent to 7.96%. Therefore, it is worthy noting that the establishment of the secure channel is having an overall priority of 74.29% which in return makes the best risk countermeasure solution for the prevention of data corruption as well as Dos attacks in the NFC[11]. Risk Assessment & Multi-Criteria Decision Techniques Essay. From the analysis therefore the best solution for the dos attacks and data corruption prevention is the establishment of the secure channels which according to the analysis, it has a priority of 74.29%. All type of attacks in the NFC communication such as the eavesdropping, and many others are able to be prevented by the solution. The protocol which could be utilized in the establishment of the secure channel in the NCF is the Diffie-Hellman which is based on the RSA or the Elliptic Curves Cryptography. As from the data which was collected from interviews, the participants made an overall suggestion that 3DES to be used for shorter transaction which requires shorter time of response and RSA to be used for longer response time for transactions.
CONCLUSION
From the analysis and evaluation, it is noted that, in this research, there are two contributions which have been made, using the MIDAS system, a guideline solution is proposed in order to put security to the NFC application. As from the analysis, the ECC as well as the AES are considered to be the best techniques for the establishment of the secure channel in the NFC and also in the prevention of the data corruption and the DOS attacks in the NFC [13]. It is found out that the results, findings as well as the cryptographic techniques are all similar and they correlate to each other as the standards for the mechanism of NFC. On the basis of the research significance, and methods, the possibility of the NFC security risk as been determined by evaluation of the risk by the use of risk assessment methods whereby the highest risk which are determined was data corruption and dos attacks. The impediment of this exploration includes the quantity of members that take an interest in online review and the quantity of NFC specialists. Risk Assessment & Multi-Criteria Decision Techniques Essay. The result results from hazard evaluation procedure is associated to the quantity of testing size. Diverse examining size or gathering can have affected the result results. For further research, distinctive hazard appraisal technique can be utilized to assess the security chances in NFC. Other MCDM strategies can be considered to actualize in this examination as to choose the best answer for counteract security assaults. Other than sensitive use of NFC, other NFC application can be tried as to decide the probability of its security dangers.
ORDER A CUSTOM-WRITTEN, PLAGIARISM-FREE PAPER HERE
References
[1]B. Borchert and M. Günther, “Indirect NFC-Login on a Non-NFC Device using an NFC-Smartphone”, International Journal of Intelligent Computing Research, vol. 4, no. 4, pp. 358-364, 2013. Available: 10.20533/ijicr.2042.4655.2013.0047.
[2]L. Francis, G. Hancke, K. Mayes and K. Markantonakis, “On the security issues of NFC enabled mobile phones”, International Journal of Internet Technology and Secured Transactions, vol. 2, no. 34, p. 336, 2010. Available: 10.1504/ijitst.2010.037408. Risk Assessment & Multi-Criteria Decision Techniques Essay.
[3]K. Grassie, “Easy handling and security make NFC a success”, Card Technology Today, vol. 19, no. 10, pp. 12-13, 2015. Available: 10.1016/s0965-2590(08)70134-8.
[4]Y. Jang, S. Chang and Y. Tsai, “Smartphone security: understanding smartphone users’ trust in information security management”, Security and Communication Networks, vol. 7, no. 9, pp. 1313-1321, 2013. Available: 10.1002/sec.787.
[5]H. Kim, “Investigation on NFC-based Security System for Smart Work”, Journal of Security Engineering, vol. 11, no. 3, pp. 263-272, 2014. Available: 10.14257/jse.2014.06.06.
[6]A. Mylonas, A. Kastania and D. Gritzalis, “Delegate the smartphone user? Security awareness in smartphone platforms”, Computers & Security, vol. 34, pp. 47-66, 2013. Available: 10.1016/j.cose.2012.11.004. Risk Assessment & Multi-Criteria Decision Techniques Essay.
[7]J. Geon Pak, B. Ram Lee and M. Suk Lee, “Implementation of Mobile Smart Key System using the NFC Function of the Smartphone”, International Journal of Engineering & Technology, vol. 7, no. 44, p. 1, 2018. Available: 10.14419/ijet.v7i4.4.19589.
[8]S. Poddar, “Central Locker System for shopping mall using NFC Based Smartphone”, Transactions on Networks and Communications, vol. 2, no. 5, 2014. Available: 10.14738/tnc.25.520.
[9]”NFC Phones Raise Opportunities, Privacy And Security Issues”. [Online]. Available: https://cdt.org/blog/nfc-phones-raise-opportunities-privacy-and-security-issues/. [Accessed: 2019].
[10]”Security Risks of Near Field Communication Technology”. [Online]. Available: http://nearfieldcommunication.org/nfc-security-risks.html. [Accessed: 2019].
[11]”Security Issues in Mobile NFC Devices | Request PDF”. [Online]. Available: https://www.researchgate.net/publication/266557612_Security_Issues_in_Mobile_NFC_Devices. [Accessed: 2019].
[12]”Concerns Related to NFC Technology for Payments [Updated 2019]”. [Online]. Available: https://resources.infosecinstitute.com/nfc-technology-payments-concerns/. [Accessed: 2019].
[13]”Mobile Payments: Risk, Security and Assurance Issues”. [Online]. Available: https://www.isaca.org/Groups/Professional-English/pci-compliance/GroupDocuments/MobilePaymentsWP.pdf. [Accessed: 2019]. Risk Assessment & Multi-Criteria Decision Techniques Essay.